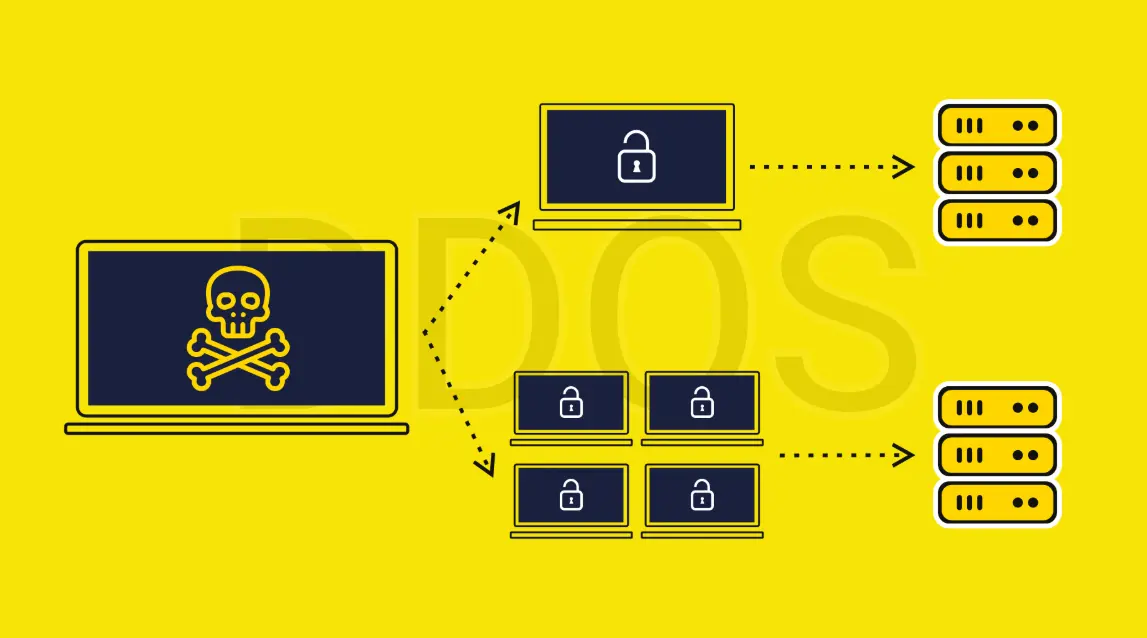
DDoS, or Distributed Denial of Service, is a type of cyber attack where multiple compromised devices are used to flood a target server, website, or network with excessive traffic. This overwhelming volume of requests exhausts the target’s resources, such as bandwidth or processing power, making it inaccessible to legitimate users. Common motivations include extortion, activism, or competition sabotage. Attackers often leverage botnets—networks of infected computers—to coordinate the assault, which can range from simple volumetric floods to sophisticated application-layer exploits. Effective mitigation requires robust defenses like traffic filtering, rate limiting, and redundancy in infrastructure.
Table of contents
- Part 1: Create a Ddos quiz in minutes using AI with OnlineExamMaker
- Part 2: 20 Ddos quiz questions & answers
- Part 3: Automatically generate quiz questions using AI Question Generator
Part 1: Create a Ddos quiz in minutes using AI with OnlineExamMaker
When it comes to ease of creating a Ddos assessment, OnlineExamMaker is one of the best AI-powered quiz making software for your institutions or businesses. With its AI Question Generator, just upload a document or input keywords about your assessment topic, you can generate high-quality quiz questions on any topic, difficulty level, and format.
Overview of its key assessment-related features:
● AI Question Generator to help you save time in creating quiz questions automatically.
● Share your online exam with audiences on social platforms like Facebook, Twitter, Reddit and more.
● Instantly scores objective questions and subjective answers use rubric-based scoring for consistency.
● Simply copy and insert a few lines of embed codes to display your online exams on your website or WordPress blog.
Automatically generate questions using AI
Part 2: 20 Ddos quiz questions & answers
or
1. Question: What does DDoS stand for?
A. Distributed Denial of Service
B. Direct Data Over System
C. Digital Defense Operating System
D. Data Denial Over Server
Answer: A
Explanation: DDoS stands for Distributed Denial of Service, which involves multiple compromised systems attacking a single target to overwhelm it.
2. Question: Which of the following is a common type of DDoS attack?
A. Phishing
B. UDP Flood
C. Ransomware
D. Malware installation
Answer: B
Explanation: A UDP Flood is a volumetric DDoS attack that floods a target with User Datagram Protocol packets, consuming bandwidth.
3. Question: How does a DDoS attack primarily work?
A. By encrypting data
B. By overwhelming the target’s resources
C. By stealing user credentials
D. By altering website content
Answer: B
Explanation: DDoS attacks work by flooding the target with traffic from multiple sources, overwhelming its bandwidth or resources and making it unavailable.
4. Question: What is the main difference between a DoS and a DDoS attack?
A. DoS is faster
B. DDoS uses a single source, DoS uses multiple
C. DoS uses multiple sources, DDoS uses a single source
D. DDoS involves distributed networks of compromised devices
Answer: D
Explanation: DDoS attacks use a network of compromised devices (botnets) across multiple locations, while DoS attacks come from a single source.
5. Question: Which protocol is often exploited in amplification DDoS attacks?
A. HTTP
B. DNS
C. FTP
D. SMTP
Answer: B
Explanation: DNS amplification attacks exploit the DNS protocol by sending small queries that result in large responses, overwhelming the target.
6. Question: What is a botnet in the context of DDoS?
A. A network of legitimate servers
B. A group of compromised devices controlled remotely
C. A type of firewall
D. An encryption tool
Answer: B
Explanation: A botnet is a collection of hijacked devices infected with malware, used to launch coordinated DDoS attacks.
7. Question: Which layer of the OSI model is most affected by application-layer DDoS attacks?
A. Physical layer
B. Network layer
C. Application layer
D. Data link layer
Answer: C
Explanation: Application-layer DDoS attacks target the seventh layer of the OSI model, exhausting resources like CPU or memory through HTTP requests.
8. Question: What is rate limiting as a DDoS mitigation strategy?
A. Blocking all traffic
B. Limiting the number of requests from a single IP
C. Increasing server capacity
D. Encrypting data transfers
Answer: B
Explanation: Rate limiting restricts the amount of traffic from any single source, helping to prevent overwhelming the server during an attack.
9. Question: In a SYN flood DDoS attack, what is being exploited?
A. TCP handshake process
B. UDP packets
C. DNS queries
D. HTTP responses
Answer: A
Explanation: A SYN flood exploits the TCP three-way handshake by sending numerous SYN packets without completing the connection, exhausting server resources.
10. Question: Which of the following is a sign of a DDoS attack?
A. Sudden increase in website traffic
B. Regular software updates
C. Improved server performance
D. Decreased email spam
Answer: A
Explanation: A sudden and unexplained spike in traffic is a common indicator of a DDoS attack, as it aims to overload the system.
11. Question: What role does a CDN play in DDoS protection?
A. It encrypts all data
B. It distributes traffic across multiple servers
C. It blocks all incoming packets
D. It identifies malware
Answer: B
Explanation: A Content Delivery Network (CDN) mitigates DDoS by spreading traffic across a global network of servers, reducing the load on any single point.
12. Question: Which attack vector is used in a HTTP flood?
A. Sending malformed packets
B. Overloading with legitimate HTTP requests
C. Encrypting server files
D. Stealing database information
Answer: B
Explanation: An HTTP flood involves sending a high volume of legitimate HTTP requests to exhaust the web server’s resources.
13. Question: What is the purpose of a DDoS scrubber?
A. To clean infected files
B. To filter malicious traffic before it reaches the target
C. To speed up website loading
D. To monitor user logins
Answer: B
Explanation: A DDoS scrubber analyzes and filters incoming traffic, removing malicious packets and allowing legitimate traffic to pass through.
14. Question: Which organization might use DDoS attacks for cyber warfare?
A. Local businesses
B. Nation-states or hacktivist groups
C. Educational institutions
D. Online retailers
Answer: B
Explanation: Nation-states or hacktivist groups often use DDoS attacks as part of cyber warfare to disrupt services or make political statements.
15. Question: How can organizations prepare for a DDoS attack?
A. By ignoring traffic patterns
B. By implementing firewalls and monitoring tools
C. By reducing server security
D. By sharing passwords publicly
Answer: B
Explanation: Preparing involves using firewalls, intrusion detection systems, and traffic monitoring to detect and respond to potential DDoS threats early.
16. Question: What is a zero-day DDoS attack?
A. An attack that occurs at midnight
B. An exploit of a previously unknown vulnerability
C. A attack lasting 24 hours
D. A simulated training exercise
Answer: B
Explanation: A zero-day DDoS attack leverages vulnerabilities that are unknown to the vendor, making it harder to defend against.
17. Question: Which of the following is not a DDoS mitigation technique?
A. Traffic analysis
B. Rate limiting
C. Password cracking
D. Anomaly detection
Answer: C
Explanation: Password cracking is unrelated to DDoS mitigation; it is a method used in credential attacks, not for handling denial-of-service scenarios.
18. Question: In a volumetric DDoS attack, what is the primary goal?
A. To steal data
B. To consume all available bandwidth
C. To crash applications
D. To spread viruses
Answer: B
Explanation: Volumetric attacks aim to saturate the target’s bandwidth with massive amounts of traffic, making the network inaccessible.
19. Question: What does “amplification” mean in DDoS contexts?
A. Making the attack louder
B. Using smaller requests to generate larger responses
C. Increasing server speed
D. Reducing traffic volume
Answer: B
Explanation: Amplification involves sending small queries to open servers that respond with much larger replies, directed at the target to amplify the attack.
20. Question: Why are IoT devices often used in DDoS botnets?
A. They are highly secure
B. They have weak security and are always connected
C. They process data quickly
D. They are expensive to maintain
Answer: B
Explanation: IoT devices are frequently targeted for botnets due to their weak default security settings and constant internet connectivity, making them easy to compromise.
or
Part 3: Automatically generate quiz questions using OnlineExamMaker AI Question Generator
Automatically generate questions using AI